1.
Introduction
Over the past few decades, considerable attention has been paid to the rigorous analysis of mathematical models describing tumor growth and great progress has been achieved. Most work in this direction focuses on the sphere-shaped or nearly sphere-shaped tumor models; see [1,2,3,4,5,6,7,8,9] and the references therein. Observing that the work concerning models for tumors having different geometric configurations from spheroids is less frequent, in this paper we are interested in the situation of tumor cord–a kind of tumor that grows cylindrically around the central blood vessel and receives nutrient materials (such as glucose and oxygen) from the blood vessel [10]. The model only describes the evolution of the tumor cord section perpendicular to the length direction of the blood vessel due to the cord's uniformity in that direction. Assume that the radius of the blood vessel is r0 and denote by J and Γ(t) the section of the blood vessel wall and the section of the exterior surface of the tumor cord, respectively, then J={x∈R2;|x|=r0}. We also denote by Ω(t) the region of the section of the tumor cord, so that Ω(t) is an annular-like bounded domain in R2 and ∂Ω(t)=J∪Γ(t). The mathematical formulation of the tumor model under study is as follows:
Here, σ and p denote the nutrient concentration and pressure within the tumor, respectively, which are to be determined together with Ω(t), and c=Tdiffusion /Tgrowth is the ratio of the nutrient diffusion time scale to the tumor growth (e.g., tumor doubling) time scale; thus, it is very small and can sometimes be set to be 0 (quasi-steady state approximation). Assume that the time delay τ is reflected between the time at which a cell commences mitosis and the time at which the daughter cells are produced and ξ(s;x,t) represents the cell location at time s as cells are moving with the velocity field →V, then the function ξ(s;x,t) satisfies
In other words, ξ tracks the path of the cell currently located at x. (1.3) is further derived from (1.10) under the assumption of a porous medium structure for the tumor, where Darcy's law →V=−∇p holds true. Because of the presence of time delay, the tumor grows at a rate that is related to the nutrient concentration when it starts mitosis and a combination of the conservation of mass and Darcy's law yields (1.2), in which μ represents the growth intensity of the tumor and ˜σ is the nutrient concentration threshold required for tumor cell growth. Additionally, ˉσ is the nutrient concentration in the blood vessel, ˉσ>˜σ, V, κ and →ν denote the normal velocity, the mean curvature and the unit outward normal field of the outer boundary Γ(t), respectively, →n denotes the unit outward normal field of the fixed inner boundary J, and γ is the outer surface tension coefficient. Thus, the boundary condition σ=ˉσ on J indicates that the tumor receives constant nutrient supply from the blood vessel, ∂→νσ=0 on Γ(t) implies that the nutrient cannot pass through Γ(t), ∂→np=0 on J means that tumor cells cannot pass through the blood vessel wall, p=γκ on Γ(t) is due to the cell-to-cell adhesiveness, and V=−∂→νp on Γ(t) is the well-known Stefan condition representing that the normal velocity of the tumor cord outer boundary Γ(t) is the same with that of tumor cells adjacent to Γ(t). Finally, σ0(x), p0(x), Γ0 are given initial data and Ω(t)=Ω0 for −τ≤t≤0.
Before going to our interest, we prefer to recall some relevant works. Models for the growth of the strictly cylindrical tumor cord were studied in [11,12,13]. For the model (1.1)–(1.9) without the time delay, if c=0, Zhou and Cui [14] showed that the unique radially symmetric stationary solution exists and is asymptotically stable for any sufficiently small perturbations. Meanwhile, if c>0, Wu et al. [15] proved that the stationary solution is locally asymptotically stable provided that c is small enough. On the other hand, Zhao and Hu [16] considered the multicell spheroids with time delays. For the case c=0, they analyzed the linear stability of the radially symmetric stationary solution as well as the impact of the time delay.
Motivated by the works [14,15,16], here we aim to discuss the linear stability of stationary solutions to the problem (1.1)–(1.9) with the quasi-steady-state assumption, i.e., c=0, and investigate the effect of time delay on tumor growth. Our first main result is given below.
Theorem 1.1. For small time delay τ, the problem (1.1)–(1.9) admits a unique radially symmetric stationary solution.
Next, in order to deal with the linear stability of the radially symmetric stationary solution, denoted by (σ∗,p∗,Ω∗), where Ω∗={x∈R2: r0<r=|x|<R∗}, we assume that the initial conditions are perturbed as follows:
The linearized problem of (1.1)–(1.9) at (σ∗,p∗,Ω∗) is then obtained by substituting
into (1.1)–(1.9) and collecting the ε-order terms. Now, we can state the second main result of this paper.
Theorem 1.2. For small time delay τ, the radially symmetric stationary solution (σ∗,p∗,Ω∗) of (1.1)–(1.9) with c=0 is linearly stable, i.e.,
for some positive constants C and δ.
Remark 1.1. Compared with results of the problem modeling the growth of tumor cord without time delays in [14], the introduction of the time delay does not affect the stability of the radially symmetric stationary solution even under non-radial perturbations. However, as we shall see in Subsection 3.3, the numerical result shows that adding time delay would result in a larger stationary tumor. Moreover, the stronger the growth intensity of the tumor is, the greater the influence of time delay on the size of the stationary tumor is.
Remark 1.2. Compared with results of the nearly sphere-shaped tumor model with time delays in [16], which state that the radially symmetric stationary solution is linearly stable for small μ in the sense that limt→∞max0≤θ≤2π|ρ(θ,t)−(a1cosθ+b1sinθ)|=0 for some constants a1 and b1, the radially symmetric stationary solution of tumor cord with the time delay is linearly stable for any μ>0 in the normal sense.
This paper is organized as follows. In Section 2, we give the proof of Theorem 1.1 by first transforming the free boundary problem into an equivalent problem with fixed boundary and then applying the contraction mapping principle combined with Lp estimates to this fixed boundary problem. In Section 3, we prove Theorem 1.2 and Remark 1.1 by first introducing the linearization of (1.1)–(1.9) at the radially symmetric stationary solution (σ∗,p∗,Ω∗), and then making a delicate analysis of the expansion in the time delay τ provided that τ is sufficiently small. A brief conclusion in Section 4 completes the paper.
2.
Radially symmetric stationary solutions
In this section, we study radially symmetric stationary solutions (σ∗,p∗,Ω∗) to the system (1.1)–(1.9), which satisfy
where Δr is the radial part of the Laplacian in R2.
Before proceeding further, let us recall that the modified Bessel functions Kn(r) and In(r), standard solutions of the equation
have the following properties:
and
Proof of Theorem 1.1 In view of (2.5), the solution of (2.1) is clearly given by
Introducing the notations:
(2.1)–(2.4) reduces to the following system after dropping the "^" in the above variables:
It is clear that (2.12) can be solved explicitly. For convenience, we extend the solution of (2.12) outside [0, 1]:
Assume that Rmin and Rmax are positive constants to be determined later and r0<Rmin<Rmax. For any R∗∈[Rmin,Rmax], we will prove that p is also uniquely determined by applying the contraction mapping principle.
Noticing that 0 is a lower solution of (2.14), but there is no assurance that ξ(s;r,0)≤1 for −τ≤s≤0, we suppose ξ(s;r,0)∈[0,2] and take
where M>0 is to be determined. For each p∈X, we first solve for ξ from (2.14) and substitute it into (2.13), then the following system
allows a unique solution ˉp∈W2,∞[0,1]. Applying the strong maximum principle combined with the Hopf lemma to (2.1) shows that σ(r;R∗)≤ˉσ. Thus, integrating (2.17), we obtain
Define the mapping
then ‖Lp‖∈W2,∞[0,2] and ‖Lp‖W2,∞[0,2]≤2‖ˉp‖W2,∞[0,1]. Combining (2.18)–(2.20), we find
If we choose M≥M1, then Lp∈X by (2.21) and L maps X to itself.
We now show that L is a contraction. Given p(1),p(2)∈X, one can first get ξ(1),ξ(2) from the following two systems:
Integrating (2.22) and (2.23) with regard to s over the interval [−τ,0] and making a subtraction yield
for all −τ≤s≤0 and 0≤r≤1. Consequently,
Next, we substitute ξ(1),ξ(2) into (2.17) and solve for ˉp(1) and ˉp(2), respectively, then it follows from (2.17) that (ˉp(1)−ˉp(2))(1)=0, ∂∂r(ˉp(1)−ˉp(2))(0)=0 and
Using (2.24), we derive
and similarly,
where
Here, we employed the fact that
by (2.1) and σ≤ˉσ. Let M5=M2+M3+M4, then M5 is independent of τ and
which together with Lp(1)(1)=Lp(2)(1)=γ(R∗−r0)R∗ and (Lp(1))′(0)=(Lp(2))′(0)=0 implies that
Hence, if τ is sufficiently small such that 2M5τ<1, then we derive a contracting mapping L. The existence and uniqueness of p are therefore obtained.
It suffices to prove that there exists a unique R∗∈[Rmin,Rmax] satisfying (2.15). Substituting (2.16) into (2.15), we find that it is equivalent to solving the following equation for R:
Clearly,
Using Lemma 3.1 and Theorem 3.2 in [14] and the condition ˉσ>˜σ, we know that
which implies that the equation G(R,0)=0 has a unique solution, denoted by RS, and
Since
when τ is sufficiently small, ∂G(R,τ)∂R and ∂G(R,0)∂R have the same sign. Thus, G(R,τ) is monotone decreasing in R. Using the fact that G(R,τ) is continuous in τ, we further have
Hence, when τ is sufficiently small, the equation G(R,τ)=0 has a unique solution R∗. Taking Rmin=12(RS+r0) and Rmax=32RS, we complete the proof of the theorem.
3.
Linear stability
This section is devoted to the linear stability of the radially symmetric stationary solution (σ∗,p∗,Ω∗) of the problem (1.1)–(1.9) and the effect of time delay on the stability and the size of the stationary tumor. Let (σ,p,Ω(t)), given by (1.11)–(1.13), be solutions to (1.1)–(1.9), and denote by →er, →eθ the unit normal vectors in r, θ directions, respectively. Written in the rectangular coordinates in R2,
Using the notation ξ1(s;r,θ,t), ξ2(s;r,θ,t) for the polar radius and angle of ξ(s;r,θ,t), respectively, we have
Expand ξ1, ξ2 in ε as
then we derive from (1.3) and (1.13) that
It is evident that ξ20≡θ. Noticing that the equation for ξ10 is the same as that for ξ∗ in the radially symmetric case, ξ10 is independent of θ.
Substituting (1.11)–(1.13) and (3.1)–(3.5) into (1.1), (1.2), (1.4)–(1.6), using the mean-curvature formula in the 2-dimensional case for the curve r=ρ(θ):
and collecting the ε-order terms, we obtain the linearized system in BR∗×{t>0}:
Due to the presence of the time delay, the linearization problem (3.6)–(3.8) cannot be solved explicitly. Assume that ω,q, ρ and ξ11 have the following Fourier expansions:
Substituting (3.9) into (3.6)–(3.8) yields the following system in BR∗×{t>0}:
Since it is impossible to solve the systems (2.1)–(2.4) and (3.10)–(3.17) explicitly and the time delay τ is actually very small, in what follows, we analyze the expansion in τ for (2.1)–(2.4) and (3.10)–(3.17).
3.1. Expansion in τ
Let
Substitute these expansions into (2.1)–(2.4) and (3.10)–(3.17). Since an(t) and bn(t) have the same asymptotic behavior at ∞, we will only make an analysis of an(t). For this, we discuss the expansions of R∗, σ∗, p∗, An, En and an. Since the equations for the expansions of σ∗, p∗, An, En and an are the same as those in [16], here we only compute the expansions of the boundary conditions of σ∗, p∗, An and En.
● Expansions of the boundary conditions of σ∗:
It follows from (2.10) and (2.11) that
which implies
By the boundary conditions in (2.1), we find
● Expansions of the boundary conditions of p∗:
One obtains from the boundary conditions in (2.2) that
● Expansion of (2.4):
In view of (4.31) in [16], there holds
Using (3.18), we compute
A combination of (3.20) and (3.21) gives
● Expansions of the boundary conditions of An:
We derive from the boundary conditions in (3.10) that
● Expansions of the boundary conditions of En:
Substituting the expansion of En into the boundary conditions in (3.12) yields
3.2. Zeroth-order terms in τ
Collecting all zeroth-order terms in τ leads to the following system for r0<r<R0∗:
A direct calculation gives
where
Let η0n=E0n+μA0n, then we find from (3.26) and (3.28) that η0n satisfies
whose solution is
and thus,
where C1(t) and C2(t) are to be determined by the boundary conditions in (3.28). By (2.10), (3.34), (3.35) and (3.37), we get
Using (3.35) and (3.38)–(3.40), we further derive
Substituting (3.33) and (3.41) into (3.30) yields
whose solution is explicitly given by
Here,
It was proven in Lemma 4.4 of [14] that for any . Thus, we have the following:
Lemma 3.1. For any , there exists such that for all .
Lemma 3.1 shows that decays to exponentially at ; hence, when , the radially symmetric stationary solution is asymptotically stable for all .
3.3. Sign of
Recalling that , in order to see the effect of the time delay on the size of the stationary tumor, in this subsection we discuss the sign of by a theoretical analysis combined with numerical simulations.
We obtain from (3.22) that
then by using (2.6)–(2.10), (3.18), (3.19), (3.25) and (3.32), one can solve (3.45) to obtain
where
Since
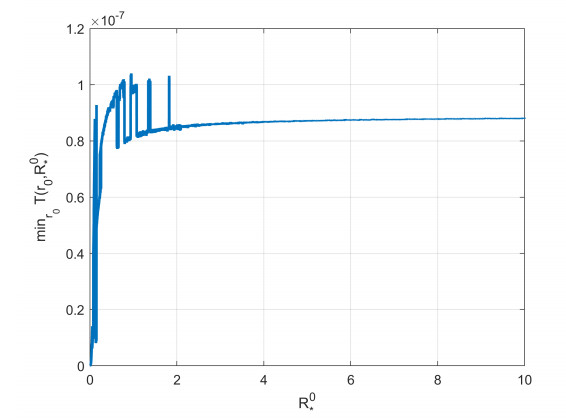
by (3.44), we know . Additionally, we numerically compute the function and find it is positive (see Figure 1). Hence, it follows from (3.46) that and is monotone increasing in .
Remark 3.1. The discussion above indicates that the presence of the time delay leads to a larger stationary tumor. Furthermore, the bigger the tumor aggressive parameter is, the greater the effect of time delay on the size of the stationary tumor is.
3.4. First-order terms in
Now, we tackle the system consisting of all the first-order terms in for :
To obtain the asymptotic behavior of as , by (3.54) and the boundedness of the modified Bessel functions and on , it suffices to analyze . For this purpose, in view of (3.52), we first compute . Solving (3.50) yields
with
where we have employed (2.8)–(2.10), (3.19), (3.36) and (3.37). Furthermore,
Next, being similar to the computation of , we set , then we derive from (3.50), (3.52) and (3.56) that
For brevity, we introduce the differential operator and write , where , , and solve the following problems, respectively:
Let us first estimate . By (3.18), (3.41) and (3.59), we have
Based on the properties of the modified Bessel functions and , the righthand side of (3.63) is less than when . Here, denotes a polynomial function of . Similar estimates can be established for and by (3.60) and (3.61).
Lemma 3.2. Consider the elliptic problem
where . If and , then the problem (3.64) and (3.65) admits a unique solution in with estimates
where the constant in (3.66) and (3.67) is independent of .
The lemma can be proven by combining the proofs of [16, Lemma 4.6] and [17, Lemma 3.2]. The details are omitted here.
Lemma 3.2 ensures the existence and uniqueness of in for . Furthermore, there holds
Obviously, the solution to the problem (3.62) has the form:
where and are determined by the boundary conditions in (3.62). Using (2.10), (3.41), (3.56), (3.57) and the boundary conditions in (3.52), we get
where , are functions of , and .
Now, since
we derive
By (3.33), (3.57) and (3.69)–(3.72), we obtain from (3.54) that
where is a known function of , , , and satisfies
Thus, using Lemma 3.1, (3.68) and (3.73) gives
In addition, for , Lemma 3.1 implies
Therefore, applying [16, Lemma 4.7] to (3.74) yields
i.e., decays exponentially as . Noticing that and have the same asymptotic behavior, we also have
Proof of Theorem 1.2 The desired result (1.14) follows from Lemma 3.1, (3.75) and (3.76). The proof is complete.
Remark 3.2. The results on tumor cord without time delays in [14] show that the radially symmetric stationary solution is asymptotically stable under nonradially symmetric perturbations. Here, our Theorem 1.2 says that such asymptotic stability does not be affected by small time delay.
4.
Conclusions
In this paper, we have investigated the effects of a time delay in cell proliferation on the growth of tumor cords, where the domain is a bounded subset in and its boundary consists of two disjoint closed curves, one fixed and the other moving and a priori unknown. The existence, uniqueness and linear stability of the radially symmetric stationary solution were studied.
Here are some interesting findings. 1) Adding the time delay would not change the stability of the radially symmetric stationary solution when compared with the same system without delay [14], but adding the time delay would result in a larger stationary tumor. The bigger the tumor growth intensity is, the greater impact that time delay has on the size of the stationary tumor. 2) By the result of [16], we know that for tumor spheroids with the same time delay, there exists a threshold for the tumor aggressiveness constant such that only for , the radially symmetric stationary solution is linearly stable under non-radial perturbations. For tumor cords, however, from Theorem 1.2 we saw that the radially symmetric stationary solution is always linearly stable, regardless of the value of . It showed that there is an essential difference between tumor cords and tumor spheroids with the same time delay.
We think that the linear stability analysis for the full system without quasi-steady state simplification, i.e., , may be very challenging, which we expect to solve in future work.
Use of AI tools declaration
The authors declare they have not used Artificial Intelligence (AI) tools in the creation of this article.
Acknowledgments
The authors would like to thank the reviewers for their valuable suggestions. This work was partly supported by the National Natural Science Foundation of China (No. 12161045 and No. 12261047), Jiangxi Provincial Natural Science Foundation (No. 20224BCD41001 and No. 20232BAB201010), the Science and Technology Planning Project from Educational Commission of Jiangxi Province, China (No. GJJ2200319), the Scientific Research Project of Hunan Provincial Education Department, China (No. 22B0725, No. 23B0670 and No. 23C0234), and the Research Initiation Project of Hengyang Normal University, China (No. 2022QD01).
Conflict of interest
The authors declare there is no conflict of interest.








 DownLoad:
DownLoad:








